Circles
Rethinking how we share and manage contact information
Daniel G. SiegelSummary
Circles proposes a decentralized, user-centric approach to managing personal contact information. Instead of relying on traditional address books or centralized social networks, users create distinct groups — referred to as circles — to organize their contacts. Each circle can have tailored access permissions, allowing users to control the specific personal information shared with each group.
By utilizing unique Circle IDs as secure identifiers, users can establish trusted connections, facilitating the sharing and automatic updating of contact details. This system aims to simplify the process of staying connected, ensuring that contact information remains current and that users maintain control over their personal data.
Almost all of today’s representations are continuations from our past — more or less direct carryovers from the physical artifacts. We kind of limit ourselves to pencil-and-paper thinking, ultimately impeding our discovery of new ideas and approaches. In other words, our current approach limits our ability to invent more powerful ways of thinking about the world. Daniel G. Siegel
Key Concepts
- Personalized contact sharing Users can segment their contacts into various circles (e.g., work, friends, family), each with customized access to personal information.
- Secure identifiers Circle IDs serve as unique, secure identifiers for each user, enabling trusted exchanges of contact information, facilitating the sharing and updating of contact details.
- Automatic updates Changes to a user's contact information are automatically propagated to all relevant circles, ensuring that contacts always have the most up-to-date details.
- Privacy control Users retain full control over who has access to their information and can easily adjust permissions as relationships evolve.
Circles reimagines the way we manage and share contact information by prioritizing user control and privacy. It addresses the common frustrations of outdated contact details and the complexities of managing multiple communication platforms. By decentralizing contact management and allowing for dynamic, context-specific sharing, Circles offers a more intuitive and secure way to stay connected.
Introduction
Whether you’re chatting with your friends, sending an email to your colleague, or calling your mom, the address book is at the core of your devices. At the same time, it’s cumbersome to manage all contact data of family, friends, and colleagues — and if you think about it, how many contact details in your address book just don’t work anymore?
This brings us to a simple question we want to explore: Can we imagine ways to restructure our digital experience to help us stay in touch with people, and to make those connections better and easier to maintain?
The contact information dilemma
A few months ago, I wanted to send an email to my brother-in-law. Just before sending it, I remembered that he’d recently switched jobs and had a new email address. What now? I had to call him before I could send the message. So much for the convenience of a quick email.
Some time before that, I travelled to Berlin for a conference and some workshops, and I thought it would be nice to catch up with old friends who live there. But had anyone moved there recently, or had anyone moved away?
My mind was giving me no answers, so I went on Facebook, and easily found individual friends and where they live, but there just wasn’t a way to get a list of all my friends who live in Berlin. I knew it ought to be possible somehow, because the data is right there on individual profiles, but Facebook just showed me ads, or old photos of other friends visiting Berlin.
I wondered, isn’t the point of a social network to help me find my friends? Maybe I’m too stupid to use it effectively?
It’s the same thing with phone numbers and email addresses; I don’t really want to know how many outdated contact details are stored in my phone and computer right now. And when I make a new friend at a party, we exchange our numbers, Facebook profiles, or Instagram handles. But what if I stop using that network or app? What if I move to a different country and change my number? What if I forget about them, distracted by the followers, friends, or contacts already in my social networks?
The way that we exchange personal contact information today is clunky, and the data we have is often outdated. It is hard to stay in touch with people, even those you like the most, especially when they live in different cities. Technology shouldn’t make this even harder than it is.
This is the topic we want to explore in this idea and hopefully come up with a few approaches to improve the situation.
Diagnosis
The issue with digital disarray
At some point you’ve probably seen the video by the Harvard Innovation Labs, demonstrating the steep progression from an ordinary office of the ’80s to today’s desktop.

The scene starts with vintage items, such as the original Macintosh, a corded phone, a fax machine, a Rolodex, the Encyclopedia or the Oxford Dictionary. Gradually, items are replaced by apps on the computer, until you are finally left with a clutter-free desktop holding only a modern laptop and a smartphone.
This video is a joy to watch. How much simpler everything is today! No need to depend on dozens of tools and devices all the time.
While watching this video I got stuck on one thing: all these devices and tools were replaced by their digital adaptations. But they were only replaced, not changed for the better — despite the thousand-fold improvement along every technological dimension.
The Rolodex was replaced by your contacts app, but its core is still the analog bundle of mostly-outdated information about your friends, colleagues, and peers.
A phone can still be dialed with a string of numbers like it was a hundred years ago, and we’re still forced to remember these numbers — or look them up when we need them.
When you open your favorite word processor you still see a blank page displaying an empty piece of paper.
Almost all of today’s representations are continuations from our past — more or less direct carryovers from the physical artifacts. We kind of limit ourselves to pencil-and-paper thinking, ultimately impeding our discovery of new ideas and approaches.
To quote Alan Kay:
It looks as though the actual revolution will take longer than our optimism suggested, largely because the commercial and educational interests in the old media and modes of thought have frozen personal computing pretty much at the “imitation of paper, recordings, film and TV” level.
In other words, our current approach limits our ability to invent more powerful ways of thinking about the world.
Our methods of digital communication are still as detached from each other as they were when there were physical machines on our desks, so it is almost impossible to transfer or exchange data between applications.
The issue with social networks
If you haven’t been living under a rock, you’ve probably witnessed how social networks gained immense popularity over the past decades. One reason is surely that you can easily impress your friends with great photos of your lunch keep contact with your friends and acquaintances even when they moved to a different city, lost their phone, changed their email address, or stopped using a certain app.
Social networks relieve you from having to manage your full address book — you only have to manage your connections inside the network. That of course requires that at least most of your social circle can be found on the specific social network. And if they are, it’s very easy to stay up to date or get in touch with your friends, colleagues, or acquaintances. In many cases, people list some of their other contact methods (like phone or email), and if they don’t, you would need to message them to ask.
There’s a downside to this approach: Most social networks and communications apps enable you to find your contacts by maintaining their own internal social graph or by uploading and storing your full address book on their servers.
The privacy problem is pretty obvious, and of course the social network is also limited to its own network, meaning you won’t be able to stay in touch with anyone who has not joined that specific social network. In other words, the number of social networks you need grows over time.
But there are several major problems. First, most social networks today restrict their external usage, in contrast to the early days when Twitter, Facebook, and others encouraged developers to use their APIs and access their networks through a plethora of tools. With the recent movement of the GDPR in Europe, many providers do provide ways to download and export personal data, but the process is very bothersome and can’t be used regularly to synchronize your contacts.
Second, each user on a social network is limited by the capabilities of that network. For example, if you would like to transmit a certain file over the messaging feature, list certain additional personal contact information, or connect to someone in a group video call, you are restricted to what that social network is offering you.
Third, most of the digital infrastructure used by social networks is centralized, closed, and controlled: a walled garden. If you don’t have access to the platform, or your friend has left the platform, there’s no way you can keep in touch.
With the plethora of social networks and apps available today, contact details are vastly scattered around. Your hiking group might be on Facebook, your best friends circle on WhatsApp, your acquaintances on Instagram, your industry peers on Mastodon, or your family chat group on Signal. Granted, this wouldn’t be a problem if everyone was on the same platform.
But the problem still arises when that platform is not accessible for some reason, like being blocked in different countries, payments people can’t afford, technological requirements such as a particular phone or specific hardware. You’re reliant on the platform and the goodwill of its operator.
We could argue that smartphone address books already solve this problem by acting as a central storage location for all contacts on all social networks. They pull data from various places and aggregate it into one location, where anyone can simply have up-to-date information about all their contacts and use that information easily. However, it is still a burden to the user to add multiple accounts when they meet someone new, to remember what contact method is best, to merge static information (like anniversaries, street addresses, or notes about a person), and to manage private information like bank accounts or PayPal accounts.
While these issues aren’t specifically about Facebook, Twitter, LinkedIn, or Instagram, the wider issue is the centralized technology created and controlled by Big Tech companies. We should acknowledge the many accomplishments and positive impact these companies have had, but it’s also important to consider the structures and business models they’ve created. Although closed systems may have short-term success, the power of open systems cannot be underestimated in the long run.
Picture this: Facebook as an open protocol instead of a closed platform. Can you imagine the freedom to stay connected with your friends on any app of your choice, seamlessly sharing messages, photos, and contacts without juggling multiple closed apps? No more pesky ads distracting you from what truly matters — maintaining your meaningful connections?
Related work
Many projects, apps, and companies have tried to improve the situation. Here are a few that we think are especially interesting or helpful.
Hermes
Hermes was an app for the Maemo/Nokia N900 platform that allowed users to synchronize data like profile photos, birthdates, websites, and more from online services such as Facebook and Twitter.
It was able to synchronize data regularly, matching existing contacts intelligently to the ones on the social networking sites.
MoID and connex.io
Both MoID and Connex.io, startups from the 2010s, tried to automatically add and synchronize contacts in your address book.
MoID tried to replace the traditional business card and eliminate the need for an exchange of info after a first contact.
The MoID app automatically collected data about all interactions with other MoID users and sorted them into a list. This allowed you to exchange contacts directly, but even days later, you could theoretically open the app to retrieve possible contacts you met at a certain event.
Once contact data had been exchanged, contact information changes would automatically be updated and synchronized.
On the other hand, Connex.io was a service that synchronized address books across multiple platforms. Users could merge their contacts from social networks (like Facebook, LinkedIn, Xing), email programs (like Outlook, Thunderbird), address book services (like Google, Apple), and their mobile devices and have them automatically kept up to date. The service synchronized the existing data for this purpose and made it available in the desired address book.
QR Codes
Many social networks have begun to add QR codes to their apps, to make it easier to exchange contact information. Both LinkedIn and WhatsApp allow you to share your QR code with another person. By scanning the QR code you are automatically directed to the other person’s profile (LinkedIn) or added to groups or single chats (WhatsApp).
This isn’t a new approach, as many people have started adding QR codes to their business cards, which are a link to their website or a social network, or contain an entire vCard contact card.
Facebook allows you to add a vast array of information to your profile, such as your work and life history, relationships, links to other social profiles, your birthday, life events, your phone number, and much more.
Adding this information allows other Facebook users to find you and stay in touch better, maybe by reminding them about your birthday or that you are related to another user. However, it’s not structured in a way that you can use it in an address book, and you can’t export your friends’ data.
Mobile address books
Both iOS and Android allow a user to add social profiles to people in their address books. They will not be updated automatically, but can make it easier to connect to a person via a specific service.
On Android, it is also possible to automatically link different profiles together (for example, a contact in your address book with a Signal or WhatsApp user), but that will only work if the specific apps are installed and configured.
Instagram, TikTok, and newer social networks
Newer social platforms, such as Instagram or TikTok, only allow you to add a short text and a link to your profile. The result is that many people get quite creative when adding their contact information.
Many use third party services such as Bitly or Linktree to combine all their social network accounts, websites, and other links into a single link that is a simple landing page. Others change that link regularly and announce the change in a post.
Magic Wormhole
26-almighty-goldfish which both acts as a password as well as an instruction to the relay server to match these two devices.
Magic Wormhole is an open source tool that enables secure file transfers between computers without the need for a central server. The transfer is initiated by generating a unique “wormhole code” on the sending computer, which is then entered into the receiving computer to establish a direct connection. The tool uses a PAKE ( Password-Authenticated Key Exchange) algorithm to create a shared key for encrypting the transferred data.
Additionally, the use of a relay server to deliver messages from one client to another is required. This allows the wormhole codes to omit IP addresses and port numbers, but the downside is that both clients must be using the same relay server and so a single point of failure exists.
Briar
Briar is a messaging app designed for activists, journalists, and anyone else who needs a safe, easy, and robust way to communicate. Unlike traditional messaging apps, Briar doesn’t rely on a central server — messages are synchronized directly between the users’ devices. If no network connection is available, Briar can sync via Bluetooth or local Wifi, keeping the information flowing in a crisis. If a network connection is available, Briar can sync via the Tor network, protecting users and their relationships from surveillance.
Backchannel
Backchannel is a digital identity system that focuses on relationships rather than traditional usernames and accounts. It was prototyped by research group Ink & Switch as an alternative to the ubiquitous concept of user profiles, both removing the need for a trusted third party and blocking various forms of impersonation attacks.
Backchannel requires a synchronous verification process for each contact, making it best suited for small, trusted groups or one-on-one communication rather than large public settings. To further emphasize relationships, Backchannel allows users to assign personalized “petnames” to their contacts using a unique key internally, rather than a phone number. This feature eliminates the need for memorizing or exchanging impersonal usernames or account numbers. However, Backchannel is not suitable for public-facing profiles, or businesses requiring a stable address, as it’s designed for private communication within small groups.
The Circles of your life
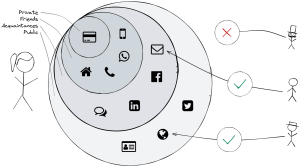
How many people’s contact details do you actually know? For most of us, the answer is probably “almost none”. You might know a street address, or a phone number, or an email address. But mostly we identify friends and contacts based on name and context. A name alone might not tell you anything, but if you know that name is related to work or your volleyball group, you can easily corroborate more details on that person (Anna from work, Benjamin my neighbor, etc.). The mapping to the actual contact detail is in many cases accomplished by an address book — whether that is a real book, the one in the phone, or a social network such as LinkedIn or Facebook.
But the reverse is true as well. The reason most of us are reluctant to change our phone numbers or email addresses is because we know there are a lot of pointers in other people’s address books containing this detail, and we want to keep them pointing to us. And no one wants the hassle of contacting everyone to update our number.
What’s needed is an address book that can keep track of your contacts, that can actually help you, and that feeds you rather than you having to feed it.

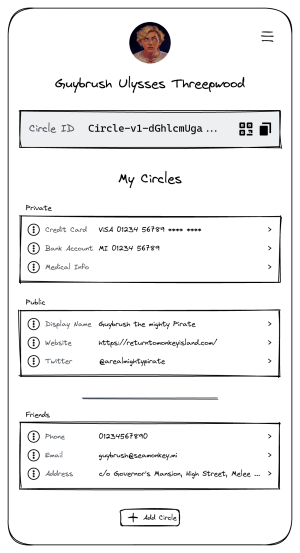
Enter Circles. With Circles you keep track of your own contact information — phone numbers, email addresses, street addresses, your birthday, anniversaries, your social network accounts, your dog’s name, and whatever else you’d like people to know about you. Additionally, a unique ID will be generated: your Circle identifier — more on that later.
Once you have entered your information, you can package different parts of it into different identities, or circles. By default, you would have two circles, one public and one private. The public one is visible to everyone, the private circles, and all other circles, would only be visible to you. Additionally, you can add circles for any group of people. For example:
- A work circle that includes your website, your work email, and Linkedin account
- A personal friends circle including your phone number, street address, and birthday
- A public circle for your work in free and open source software, containing your email address, GPG Key, Github or Gitlab account, and your website
- A private circle containing emergency information and payment information to be shared with friends on a joint trip
- A pseudonymous public circle including a different name, website, or whatever else you want to provide to that identity
Now, let’s say you meet someone. You exchange your Circle IDs (we’ll get to that in the next section), and each of you will get access to the other’s default, public Circle. Your new contact will both have access to all data stored in your public circle. At any time, you are free to move that person to a different circle, perhaps to your acquaintances circle or even your friends circle. That is all done without having to add anyone to your address book, exchange a number, or keep track of a business card.
Note that this is not bidirectional: you could leave a person in your public circle, while they include you in their friends circle.
When your acquaintance wants to contact you or look you up, their device already has all the contact information available in the circle they belong to. They can call you, text you, email you, and so on, but only if you have made the information available.
We’d only need to exchange contact information once and it would always be up to date. And you are always in control of who has your details. Things change, and perhaps you won’t want to hear from a certain person anymore; you can revoke their access easily by moving them to a different circle that can’t see your current contact information.
This approach makes life much easier for a sharer. Instead of forwarding address changes through a labyrinthine chain of email, texts, and phone calls, the sharer updates it in one central location. Anyone who needs to access the information will always have the most up-to-date version. Like magic, but with fewer rabbits and top hats.
Another advantage of this system is the control over your privacy. The sharer has fine-tuned control over who can see what information but can also make large-scale changes with ease by modifying their circles. Additionally, pseudonymity can be managed right next to the sharer’s real-life identity, making it easier to maintain privacy.
The other person also gains a few benefits, as they no longer have to worry about outdated information or storing your information manually. Instead, the data will be there already waiting to be used, and automatically updated when new information is provided.
Finally, as you only need to store a person’s Circle ID locally, you can easily combine a complete history of your contact with a person, including calls, texts, emails, making it easier to keep track of your interactions with people.
We don’t need another standalone application. We aim to create an approach that could become an underlying protocol for the way we exchange personal contact information. A protocol that can be used locally, as well as over a network, would be a versatile solution for organizing our contact information.
An ID for everything
The Circle ID serves as the unique identifier for each user. The ID is generated without the need for any prior knowledge or network connection. One possible method is UUID v4. To further reduce the chance of collisions, we can add personal identifiers such as the user’s name, birthday, or location to the UUID generation method.
However, a random ID is not enough, as it doesn’t prevent spoofing the ID and eavesdropping on any conversation. To prevent spoofing, we want to create a derived one-way hash of a public key, and use that as the Circle ID. If the public key can be exchanged later on, then it can easily be hashed to verify that it belongs to the intended recipient. Eavesdropping can be prevented by generating a shared symmetric key that can be used to create a secure end-to-end encrypted communication channel.
The Circle ID could also include a version number for forwards capability, or be prepended with recognized characters, for example: Circle-v1-dGhlcmUgaXMgbm8gc3dlZGlzaCBjb25zcGlyYWN5Cg==.
The Circle ID itself is not something that users are expected to remember, however, as it is a unique ID, we can use it to search for a specific person. It would make sense to provide readable representations of it, perhaps by using Proquints, or a word list like Bitcoin’s BIP39, or the PGP word list. Additionally, a visual representation of the ID, such as a QR code, is also feasible and can be easily displayed on a phone screen or business card.

This approach has many similarities with Public Key Infrastructure systems (such as PGP/OpenPGP), and we might even be able to build a similar system based on OpenPGP. But PKI tools are quite complex, sometimes cumbersome, and require deep knowledge of how to handle private and public keys. As we’ve seen in the past few years, many blockchain users have had problems keeping their private keys secure.
We’d like to see a system designed for trusted connections, including required recognition of all your contacts, that should not require extra work on behalf of the user, instead being a core component of the underlying system. This includes replacing and updating your keys when you switch to a new device, lose one of your devices, or a different cryptographic algorithm is needed.
In conclusion, the Circle ID serves as the primary means of finding and sharing contact information between users.
Exchanging circles (and contact information)
Contact information is not typically locked in a safe; it is shared with people who have a legitimate interest in knowing it as well as the right to access it. However, it’s important to ensure that the contact information never leaves the user’s control in an unencrypted form and that the identity of the person you are communicating with has always been verified.
There are several ways in which contact information can be exchanged. The most common method is a centralized approach, where a single central server acts as a hub for all communication. All contact information and messages are sent to this central server, which then redistributes them. This approach is used by popular social networks and messaging platforms like Signal, WhatsApp, and Facebook. However, there are some drawbacks to centralization: if the central server fails, all communication will be disrupted, and centralized servers can also be easily blocked as their location is known.
A federated network, such as XMPP (Jabber) or Mastodon, offers a more efficient solution to the problems previously discussed. In these networks, you have multiple servers to communicate with, providing more options and reducing dependence on a single server. However, it’s important to note that you always need an active network connection to your server, and it requires technical expertise to keep it running. Additionally, federated networks can still be blocked or disrupted if authorities identify and block a major server. This could require users to search for alternative servers.
Peer-to-peer networks offer a different approach, as they allow for direct communication between users without the need for servers. Briar or Bitmessage are examples of this kind of network. However, peer-to-peer networks have their own challenges. For example, users must be continuously connected to the network in order to send and receive messages. If a user goes offline, contact synchronization is not possible (at least not without caching or the capability to forward messages). This might not be an issue if you are able to use a local network, or Bluetooth, or are able to pass messages manually. But if you’re at a distance and one of the peers is currently not connected, you need a relay server to store and forward messages until the peer reappears. Briar allows you to relay messages through mutually trusted peers. Magic Wormhole on the other hand makes use of a relay server to find other peers and exchange information for a direct connection.
Many exchanges of contact information start with a face-to-face conversation. We can take advantage of this, as it ensures you’re connecting with the right person. Each of the parties can exchange their Circle ID by scanning a QR code (acting as a one-time invitation code) from the other person’s device.
Once both users pass their code to the other, both devices create a shared symmetric key using a PAKE protocol (like SPAKE2). The key is a unique identifier that can then be used to generate a secure end-to-end encrypted connection.
It should be noted that this key could also be reused or combined with other encryption methods (like PGP) to encrypt any conversation between users. This would also be possible over communication methods not under our control, like Facebook or WhatsApp chats.
As it is not always possible to meet face to face, an exchange of Circle IDs should also be possible by other means, such as a chat, email, phone call, or perhaps a message in the bottle, even though this adds to the difficulty of ensuring that the conversation is private and the uncertainty over whether you’re talking to the right person.
It is also possible to utilize additional verification that does not rely on the secrecy of the channel used (like the Diffie–Hellman key exchange or the way Briar makes use of the Tor network and a briar link to add people to a network).
The Circles protocol needs to be flexible enough to be implemented over local networks (Wifi, Bluetooth, NFC) as well over the Internet. The actual connection method should not matter, as you always assume that exchanged data can be read by untrusted participants, even if they can’t make sense of the encrypted data.
As a final note, if you just want to follow the public profile of a person, it would be possible to relax the requirements of a key exchange and just have access to the publicly available information.
Staying up to date
When both peers have established their symmetric key, they establish a secure connection and exchange the contact data, depending on which circle they belong to. The circle can be updated anytime, and you might decide to upgrade or downgrade a person to a different circle at any time.
Perhaps you no longer want your contact information to be accessible by someone who has become hostile, and the system should be able to handle the situation efficiently, guaranteeing that no new information is shared with that person.
The exchange could happen via any peer-to-peer network, but this would require an active network connection from all participants. Naturally, contact information doesn’t get updated all that often, and a delay in making the exchange is certainly acceptable.
We could also think about using relay servers to store and cache updates, and deliver them to a peer when they check for updates. In such a case, the data to be updated could be encrypted, signed, and made available publicly on the relay server for a specific time. The usage of such a relay server would make many things easier, like allowing updates even when a peer is not available, but it also poses a few challenges. For example, an attacker could draw conclusions on who’s in contact with whom, or how many peers belong to a circle. The usage of a relay server to distribute contact updates must be a carefully considered choice.
Problems
A few problems have come up, although this is not a comprehensive list of them. We’d love to hear any thoughts you have so we can include them here.
Multiple devices
Most people possess several devices they use to stay in contact with their friends. It’s quite straightforward to use the Circles protocol on many devices, by creating a shared symmetric key for each device combination, and group them together with the Circle ID. Each device could update itself from the peer or from a linked device. If a device gets lost or stolen, or simply won’t be used anymore, it still has access to the user’s Circle IDs and any shared information, introducing potential security problems and data leaks.
We could also follow the example of the Signal protocol, which uses a different public key for each device.
Hostile people and data leakage
Sometimes friendships end. How would we deal with a person who becomes hostile towards us? While it’s easy to downgrade a person to the public circle and therefore restrict their access to up-to-date information, any information they previously had access to might still be misused. Even if the protocol restricts the availability of information, perhaps by not showing the telephone number when calling, the underlying communication channel still needs that information, so it doesn’t take much to grab it.
This problem already exists today, and perhaps the best solution is simply to block certain people.
Encryption with expiry date
As contact information can be distributed over unsecure channels, an attacker has an opportunity to store the packages. Without a shared key, they wouldn’t be able to decrypt the information, but if they gained access to a person’s device, an attacker would be able to access the existing information.
Our suggestion is to employ protocols with perfect forward secrecy, but also to rotate the shared symmetric keys at irregular intervals in order to counter this theoretical attack.
Similarly, updates should not be sent if two peers haven’t refreshed their permissions, updated their keys, or made contact in a certain period of time.
Future uses
The Circle protocol is a basic step in building a better digital experience and helping us stay in touch with people. While we’ve focused our thinking on contact information, with a few improvements there are other possible uses.
Updates and stories
Instead of only sharing contact details, we could easily share updates or stories, as we do on Instagram, TikTok, WhatsApp, or Facebook. If we shared a photo (with an access expiration date), perhaps captioned or tagged with other people’s Circle IDs, we could easily emulate the stories feature.
We could scale this approach by using a relay server to store the updates and stories, prefixed and encrypted for each user based on the appropriate circles.
Preferred contact method
Depending on your current location, work schedule, or other criteria, you could automatically tell your the contacts within a specific circle what type of communication works best for you at any given time. For example, you could tell your contacts that you can’t talk right now and a text channel is preferred instead. These channels would be prioritized in the user interface when looking up a contact.
You could also use it as a status message, as in many instant messaging services.
Forums, blogs, and group chats
Like Briar, you could use Circles as a base for forums, blogs, or group chat by indirectly sharing information via your circles. In fact, you could emulate most social media features in Circles with almost no infrastructure costs. Briar is a great inspiration in this area, and deserves more study regarding possible applications.
Temporary group circles
Sometimes you only need to group people’s contacts in a temporary context, perhaps related to a trip, a party, or a concert. It’s easy to imagine that some of the people involved wouldn’t have contact details for all other participants, especially if the group does not consist of a single group of friends. In a temporary group circle, it’s easy to ensure everyone has access to necessary contact details, as well as event details, and this would also be useful after the event, perhaps to exchange photos or to settle group expenses.
Circles in organizations
Many organizations make use of shared address books, from a single shared Excel file to an enterprise system such as Google Apps, Outlook 365, or Salesforce. Circles would have a more open approach inside an organization’s network, where everyone’s contact information is published in a public circle. This would give you a global address book inside the organization, but also enable the creation of teams or temporary group circles for individual projects.
Conclusion
Once upon a time, you had to memorize phone numbers, email addresses, or street details if you wanted to make it through daily life. If a phone number wasn’t in your personal address book, you’d be forced to consult the telephone directory or Yellow Pages. We all walked around with a bunch of our most useful phone numbers, and other details, just bouncing around in our heads.
But the actual phone number or address is unimportant when what we really need is a way to get in touch with the right person. Today, we rarely use most contact details in their raw form. We have relegated them to pure routing information to use with the appropriate communication channel (a phone number for calling, a street address for routing information, and so on).
With an approach like Circles, updating your contact information becomes a breeze; you only need to make changes in one place, and all your contacts receive the updated information. This ensures that you have control over your personal information and streamlines the process of sharing information.
From your contacts’ perspective, this eliminates the worry about having outdated information as the most up-to-date information is shared with you without you needing to store it manually. With a Circle ID, you can easily track all your past interactions with a person, making it easier to maintain better connections.
Circles offers an alternative point of view that makes staying connected easier, less stressful, and more organized. Whether you’re a social butterfly or a lone wolf, this approach offers numerous benefits that can help you maintain better relationships with your contacts. We see so much potential in this approach, and, together with your help, we aim to develop this idea much further.
Big Idea Initiative is all about making connections, and sharing knowledge, thoughts, and ideas that support deep thinking and collaboration. Our goal is to create a space that sparks thinking and conversations among people whose ideas might benefit each other, even if they’re working on completely unrelated topics. We think that pushing back the limits of possibility will come as a result of the connections that diverse collaborators make together. Identifying these connections will bring the big ideas our world needs.
We need your help! If you…
- have questions or feedback about this work
- want to improve, develop, or add to this idea
- want to sponsor a prototype of this idea
we invite you to contact us: hello@bigideainitiative.org.